Imagine this: you're wowing potential buyers on your G2 Profile with custom content, product screenshots, engaging videos, transparent pricing, and insightful reviews. Your profile is a comprehensive resource, offering everything buyers need to make informed decisions. Yet, amidst this wealth of information, there's one piece of information missing — a necessity in buyer considerations: security and compliance.
Security and compliance plays a significant role in software purchasing deals
As technology continues to evolve, so does the need for foolproof security. According to our 2024 Software Buyer Behavior Report, 97% of users involved a security stakeholder in their buying process – up from 86% in 2023. And don’t just take our word for it – think about your last software evaluation, whether you were the seller or the buyer. You most likely had a security checkpoint to complete along the way to seal the deal.
Recognizing the crucial role security plays in the deal cycle, G2 has brought the first security section to G2 Profiles. Sellers can seamlessly share their security posture with buyers directly from G2. For busy software buyers with many requirements to think about during their research and software purchase, this new profile addition makes it easy to find notable security and compliance documentation while they are evaluating software on G2.
Stand out from the crowd and give buyers access to security info from Whistic or SafeBase
With a visual security icon displayed on G2 Profiles, G2 customers who are also Whistic, SafeBase, Vanta, Drata, Conveyor, or Responsive users can:
- Highlight security qualifications: Help buyers with specific security requirements identify your solution as a potential option in their buying process.
- Add a competitive edge Many buyers consider security to be a key differentiator while evaluating solutions. Showcasing your security will allow your profile to remain competitive and transparent.
- Accelerate the security assessment process: Allowing your buyers to evaluate your security qualifications early on will enable them to complete an important step in the sales process—helping your reps close deals faster.
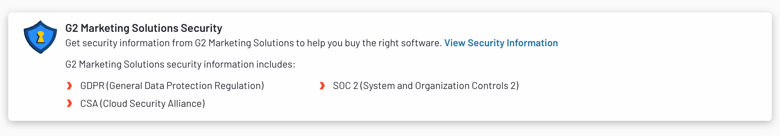
Don’t have your security up yet? Buyers interested in learning about your security standing can request this information right on your G2 Profile, and we’ll “nudge” you in your my.G2 to set it up.
How to get started with G2 Security Assessment Partners and increase your profile buyer conversion
Let’s face it. Most deals don’t happen unless security documentation has been properly vetted, so meet buyers where they’re at and provide your security information directly to them from your G2 Profile. We’ve even seen profiles with security documentation included have up to 16% higher buyer conversion than profiles without.
- For active customers of both G2 and official security providers, admins can activate this integration when logged into my.G2.com.
- Use another security provider and want to display your posture on G2? Reach out to your G2 team with the name of the security assessment vendor and we will review the request. In the meantime, you can take advantage of Whistic, SafeBase, or Conveyor for free to share your security information on G2.
- Not a G2 customer yet? Talk to a rep today to learn more and get access to this integration.
Considering that 80% of B2B software decision makers globally say their company requires a security or privacy assessment when purchasing software, it will only become increasingly crucial for vendors to demonstrate their commitment to security standards to win over buyers. Now’s your time to prove your commitment on G2 and let buyers know the steps you’ve taken to protect their data and privacy.
 by Nicole Cuillo
by Nicole Cuillo
 by Nicole Cuillo
by Nicole Cuillo
 by Nicole Cuillo
by Nicole Cuillo